标签:to
-
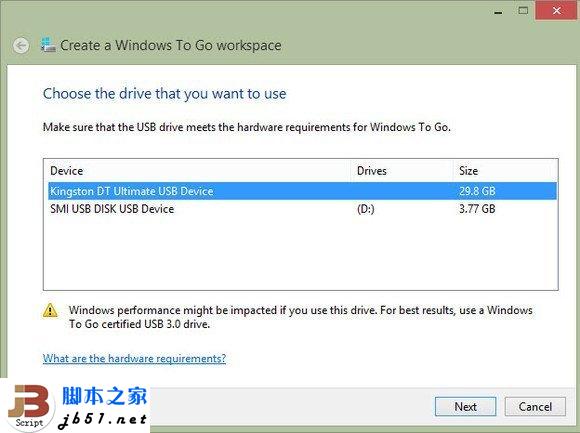
网站中运用Flash技术的优点和缺点”
Flash is a powerful web technology that achieves a high level of visual impact from the graphical point of view. Unfortunately, it is widely misused in web design. There are still many problems with Flash, especially related to usability and search e...
-
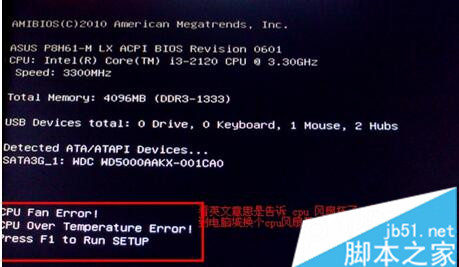
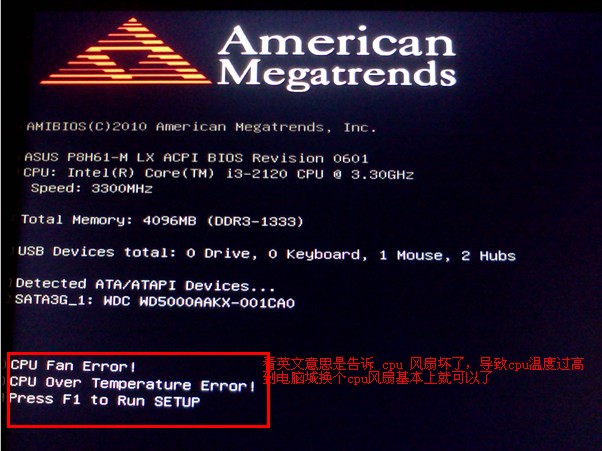
电脑开机后总显示Press F1 to Run Setup怎么办”
这篇文章主要介绍了电脑开机后总显示Press F1 to Run Setup的解决办法,遇到电脑开机后总显示Press F1 to Run Setup怎么办,小编给出了解决方法,感兴趣的小伙伴们可以参考一下...
-
开机时出现 Press F1 to Run SETUP信息的原因与解决方法”
很多网友在使用电脑过程中,偶尔会出现提示Press F1 to Run SETUP或出现press F1 to run setup press F2 to load default valuse and continue,其实注意查看上面的错误信息,一般都会有提示...
-
WordPress 2.6.1 SQL Column Truncation Vulnerability分析”
用wordpress的要注意了,不过拿我这里测试就没效果了,我从一开始就是关闭用户注册的。# WordPress 2.6.1 SQL Column Truncation Vulnerability (PoC)## found by irk4z[at]yahoo.pl# homepage: http://irk4z.wordpress.com/## this is not critic...
-
BoonEx Ray 3.5 (sIncPath) Remote File Inclusion Vulnerability”
# Name Of Script : Ray# Version : 3.5# Download From : http://get.boonex.com/Ray-v.3.5-Suite-Free# Found By : RoMaNcYxHaCkEr [ RoMaNTiC-TeaM ]# My Home Page : WwW.4RxH.CoM [ We Will Be Back Soon ] & Tryag.cc/cc [ M...
-
Mole Group Last Minute Script”
-[*] ================================================================================ [*]--[*] Last Minute Script <= 4.0 Remote SQL Injection Vulnerability [*]--[*] =============================================================...
-
Wordpress 2.6.1 (SQL Column Truncation) Admin Takeover Exploit”
#!/usr/bin/php<?php# ------------------------------------------------------------# quick'n'dirty wordpress admin-take0ver poc# by iso^kpsbr in august 2oo8 ## works w/ wordpress 2.6.1## .oO( private -- do not...
-
Poppler”
############################################################################## Felipe Andres Manzano * fmanzano@fceia.unr.edu.ar ######## updates in http://felipe.andres.manzano.googlepages.com/home ####################...
-
Mole Group Real Estate Script”
-[*] ================================================================================ [*]--[*] Real Estate Script <= 1.1 Remote SQL Injection Vulnerability [*]--[*] ==============================================================...
-
Safari Quicktime”
#!/usr/bin/perl## quickbite.pl## Safari Quicktime <= 7.3 RTSP Content-Type overflow exploit# for Mac OS X (Intel)## Tested with OS X 10.4.# On victim, browse to http://server:8080/# Binds shell on port 4444....
-
PHP 4.4.5 / 4.4.6 session_decode() Double Free Exploit PoC”
<?php //////////////////////////////////////////////////////////////////////// // _ _ _ _ ___ _ _ ___ // // | || | __ _ _ _ __| | ___ _ _ ___ __| | ___ | _ | || || _ //...
-
Bilboblog 2.1 Multiple Remote Vulnerabilities”
------------------------------------------------------------------ Name : Bilboblog 2.1 Multiples Vulnerabilities Description : Bilboblog is a small application of micro-blogging in Php / MySQL Link : http://www.t...
-
NaviCOPA Web Server 2.01 Remote Buffer Overflow Exploit (meta)”
## # This file is part of the Metasploit Framework and may be redistributed # according to the licenses defined in the Authors field below. In the # case of an unknown or missing license, this file defaults to the same # license as the co...
-
Linux Kernel”
/* Linux Kernel DCCP Memory Disclosure Vulnerability Synopsis: The Linux kernel is susceptible to a locally exploitable flaw which may allow local users to steal data from the kernel memory. Vulnerable Systems: Linux Kernel Versio...
-
Microsoft Excel Malformed Palette Record DoS PoC (MS07-002)”
MS07-002 EXCEL Malformed Palette Record Vulnerability DOS POC ###### Author ###### LifeAsaGeek at gmail.com ... and Microsoft said that vuln credit is for Greg MacManus of iDefense Labs ######################## Vul...
-
BIND 9.x Remote DNS Cache Poisoning Flaw Exploit (py)”
from scapy import *import random# Copyright (C) 2008 Julien Desfossez <ju@klipix.org># http://www.solisproject.net/## This program is free software; you can redistribute it and/or modify# it under the terms of the GNU Gen...
-
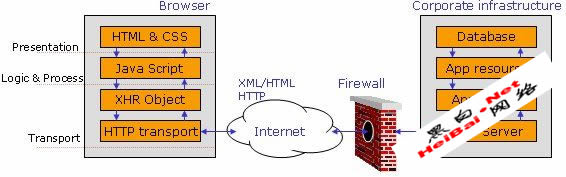
用Firefox来Hacking Web 2.0程序(图)”
Introduction //简介AJAX and interactive web services form the backbone of “web 2.0” applications. This technological transformation brings about new challenges for security professionals.This article looks at some of the methods, tools and tric...
-
记一次曲折的php入侵”
闲着无聊就又找了个站来玩玩。随便找了个。点看链接一看php的。。php的就php的吧。反正练习于是就判断是否存在注入点。and 1=1 and 1=2 返回不同。判断数据库是否大于4。0.。大于呵呵。可。。正当高行的时候。却发现无法查询。。以下是代码片段:screen.w...