标签:my
-
AuraCMS”
#!/usr/bin/perl# k1tk4t Public Security Advisory# ////////////////////////////////////////////////////////////# AuraCMS <= 2.2.2 (pages_data.php) Arbitrary Edit/Add/Delete data halaman exploit # Vendor : http://www.auracms.org/...
-
trixbox (langChoice) Local File Inclusion Exploit (connect-back)”
#!/usr/bin/perl -w# Jean-Michel BESNARD - LEXSI Audit# 2008-07-08# perl trixbox_fi.pl 192.168.1.212# Please listen carefully as our menu option has changed# Choose from the following options:# 1> Remote TCP shell#...
-
Ultrastats”
#!/usr/bin/perluse LWP::UserAgent;use Getopt::Long;## [!] Discovered.: DNX# [!] Vendor.....: http://www.shooter-szene.de | http://www.ultrastats.org# [!] Detected...: 29.06.2008# [!] Reported...: 04.07.2008# [!] Re...
-
Safari Quicktime”
#!/usr/bin/perl## quickbite.pl## Safari Quicktime <= 7.3 RTSP Content-Type overflow exploit# for Mac OS X (Intel)## Tested with OS X 10.4.# On victim, browse to http://server:8080/# Binds shell on port 4444....
-
Oracle 10g KUPM$MCP.MAIN SQL Injection Exploit”
#!/usr/bin/perl # # Remote Oracle KUPM$MCP.MAIN exploit (10g) # # Grant or revoke dba permission to unprivileged user # # Tested on "Oracle Database 10g Enterprise Edition Release 10.1.0.3.0" # # REF: http://www...
-
NaviCOPA Web Server 2.01 Remote Buffer Overflow Exploit (meta)”
## # This file is part of the Metasploit Framework and may be redistributed # according to the licenses defined in the Authors field below. In the # case of an unknown or missing license, this file defaults to the same # license as the co...
-
MS Internet Explorer (FTP Server Response) DoS Exploit”
#!/usr/bin/perl # MS 07-016 FTP Server Response PoC # Usage: ./ms07016ftp.pl [LISTEN_IP] # # Tested Against: MSIE 6.02900.2180 (SP2) # # Details: The response is broken into buffers, either at length 1024, #...
-
eNdonesia 8.4 (Calendar Module) Remote SQL Injection Exploit”
#!/usr/bin/perl#/-----------------------------------------------#| /----------------------------------------- |#| | Remote SQL Exploit | |#| | eNdonesia 8.4 Remote SQL Exploit | |#| | www.endonesia.o...
-
AlstraSoft Article Manager Pro 1.6 Blind SQL Injection Exploit”
#/usr/bin/perl#| | Author: GoLd_M#--//--># -- AlstraSoft Article Manager Pro Blind SQL Injection Exploit --#--//--> Exploit :use strict;use LWP::Simple;print "- - - - - - - - - - - - - - - - - - - - - - - - - -...
-
Bea Weblogic Apache Connector Code Exec / Denial of Service Exploit”
#// Bea Weblogic -- Apache Connector Remote Exploit -1day#// Should stack break latest Windows Server 2003 <address space randomization>#// BIG THANKS TO #// "dong-hun you"(Xpl017Elz) in INetCop - for his paper#// "T...
-
e107 Plugin BLOG Engine 2.2 Blind SQL Injection Exploit”
#!/usr/bin/perl ###################################################################################### e107 Plugin BLOG Engine v2.2 Blind SQL Injection Exploit ## ..::virangar security te...
-
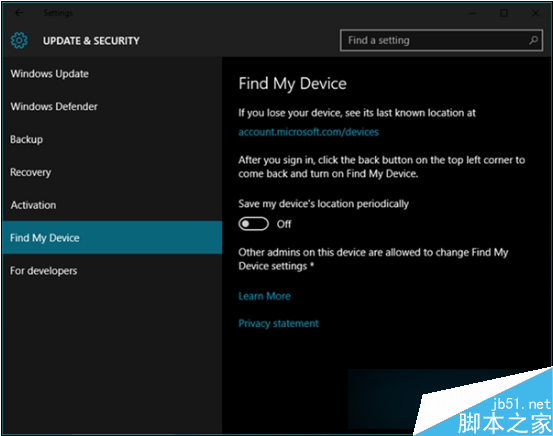
win10预览版10558中Find My Device怎么打开?win10系统寻找我的设备使用教程”
win10预览版10558新增了一个 Find My Device寻找我的设备功能,这样就可以方便用户找到自己的手机,而win10预览版10558中Find My Device是什么?本文将提供win10系统寻找我的设备使用教程供大家了解...
-
MySQL MyISAM默认存储引擎实现原理”
这篇文章主要介绍了MySQL MyISAM默认存储引擎实现原理,文中通过示例代码介绍的非常详细,对大家的学习或者工作具有一定的参考学习价值,需要的朋友可以参考下...
-
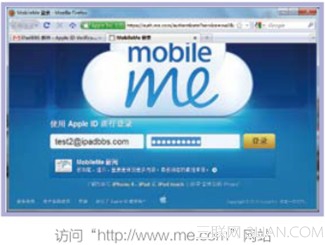
如何使用“Find My iPad”的功能”
很多新手朋友们都不知道如何使用“Find My iPad”的功能,首先在iPad中激活了Find My iPad的功能,具体的操作步骤如下,感兴趣的朋友不要错过...